pic
我草go,现在电脑没配好环境,等两天京东换货到了再复现
你这主函数保真吗
还真就是个假的主函数:
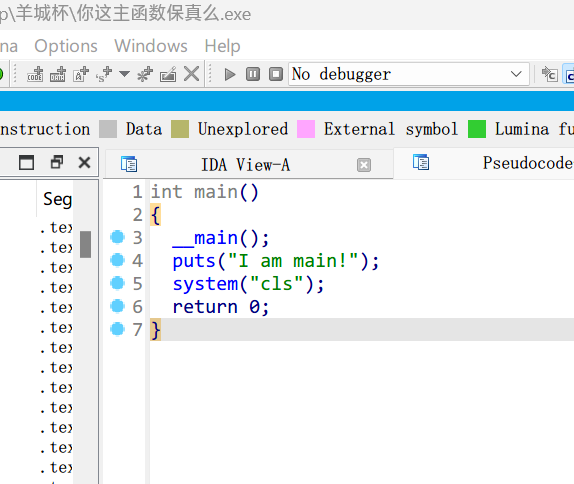
观察一下其他函数,
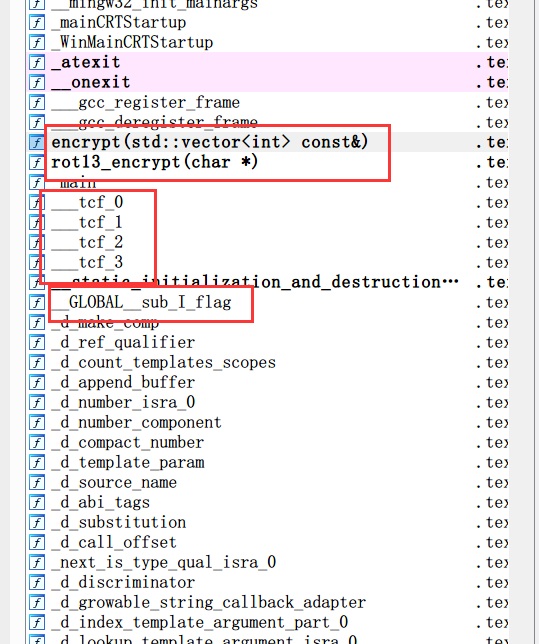
encrypt(std::vector const&)函数是个DCT, rot13_encrypt函数就是和它名字一样,rot,然后就是 tcf_0....再一个就是 GLOBALsub_I_flag函数。
Test::Test函数是输入和检测长度的功能, tcf_2函数里面却是判断正误的地 方,Test2::Test2里就是 rot,然后DCT在 tcf_3里。后来查了一下 atexit函数的作用才知道,该函数注册的函数会在程序结束的时候进行逆序的运行,逆序的序就是函数注册的顺序,那这就可以理解了,
输入的flag,先进行了rot加密,然后再来一次dct加密,最后进行比对,比对的数据就是 check数组。
exp:
import numpy as np
def idct(dct coeffs): N = len(dct coeffs)
original = np.zeros(N) PI = np.pi
for n in range(N): sum val = 0.0
for k in range(N):
Ck = (1.0 / np.sqrt(N)) if k == 0 else np.sqrt(2.0 / N) sum val += Ck * dct coeffs[k] * np.cos(PI * k * (2.0 * n +
original[n] = sum val return original
def vector to string(vec):
result = '' for val in vec:
ascii val = int(round(val)) if 32 <= ascii val <= 126:
result += chr(ascii val) return result
def rot13(input str): output = ''
for c in input str: if 'a' <= c <= 'z':
output += chr((ord(c) elif 'A' <= c <= 'Z':
output += chr((ord(c) else:
output += c return output
def main(): enc = [
513.355, -37.7986, 8.7316, -10.7832, -1.3097, -20.5779, 6.9864 15.9422, 21.4138, 29.4754, -2.77161, -6.58794, -4.22332, -7.20
-4.38138, -19.3898, 18.3453, 6.88259, -14.7652, 14.6102, 24.74
-9.75476, 12.2424, 13.4343, -34.9307, -35.735, -20.0848, 39.68 26.8296
]
original = idct(enc)
original string = vector to string(original) decrypted string = rot13(original string)
print("Decrypted string:", decrypted string)
if name == " main ": main()
#DASCTF{Wh0_1sMa1n@nd_FunnY_Dct}docCrack
附件为docm,猜测是宏代码,使用olevba提取之,
提取出来这一大坨我也看不懂是什么玩意儿的东西,总之先看看,
这里有一个xor:
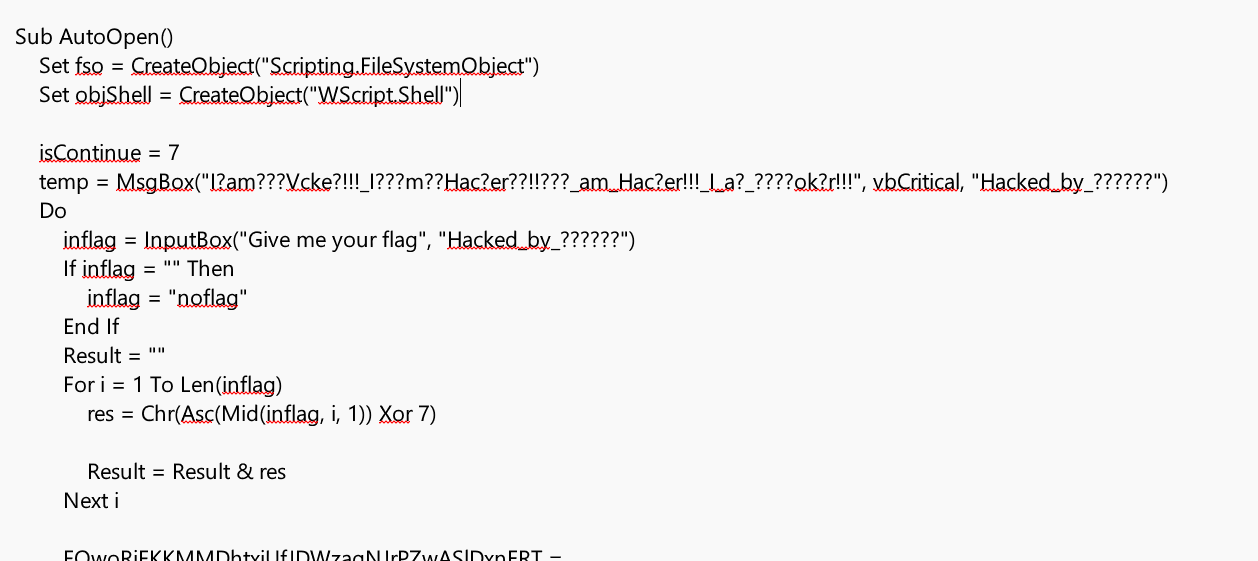
这里有一个字符串合并:
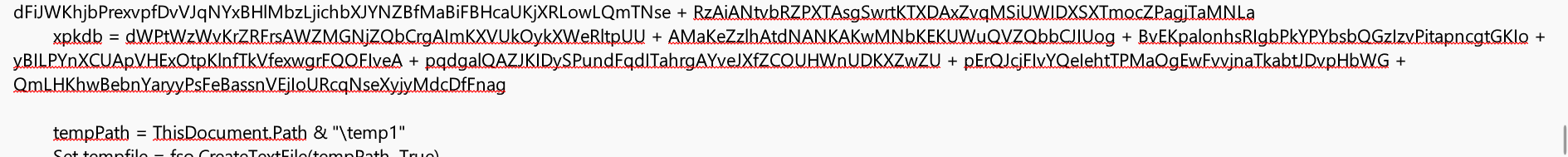
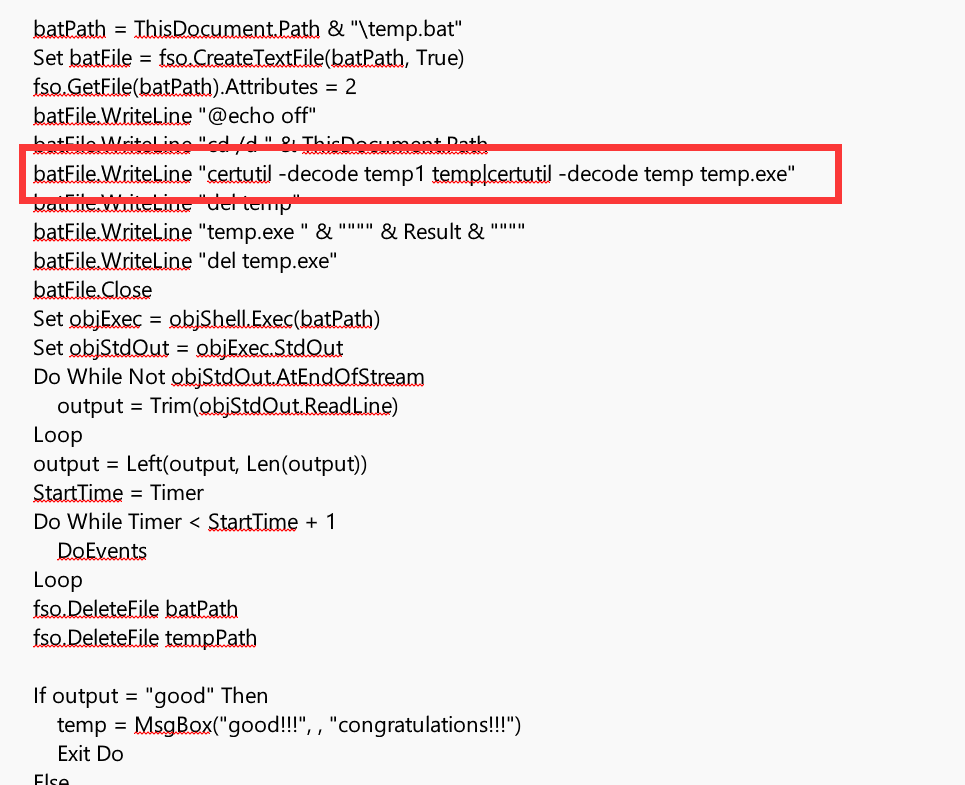
这里是打包exe然后执行:
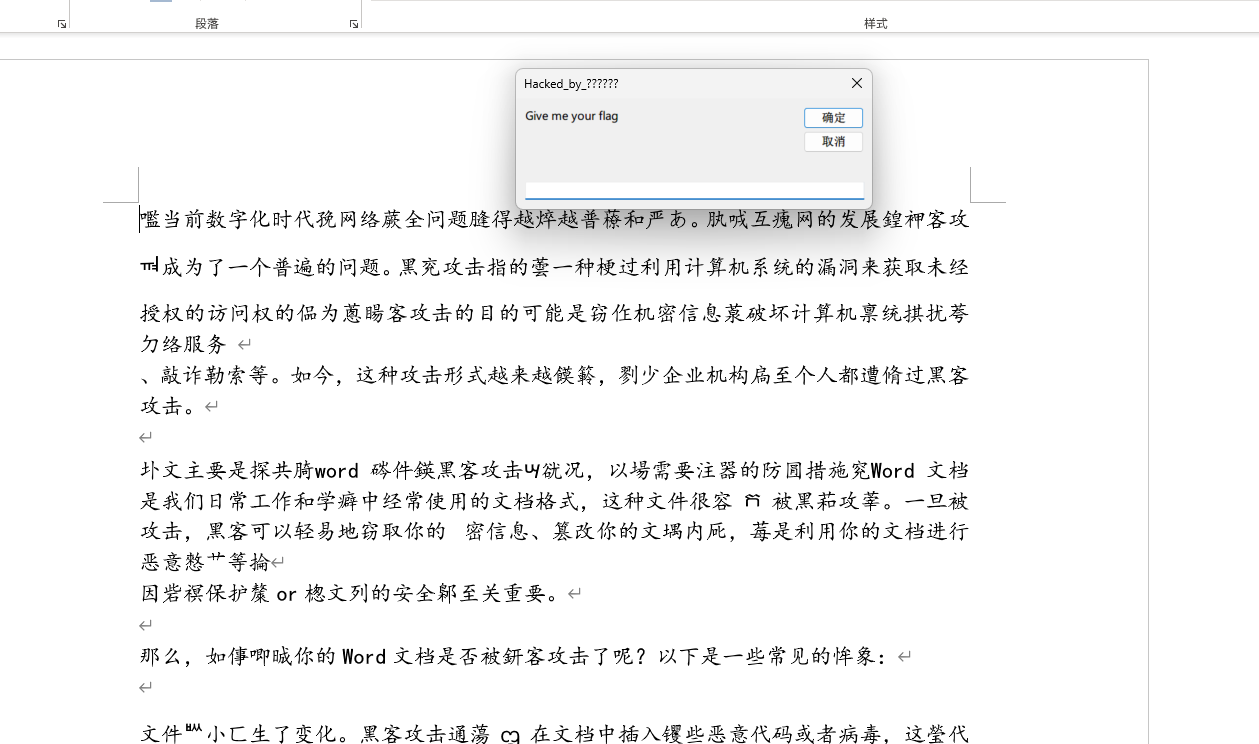
打开docm,这扑面而来的火星文给我整不会了。启用宏,出现了:
文档打开捕获到temp1文件,
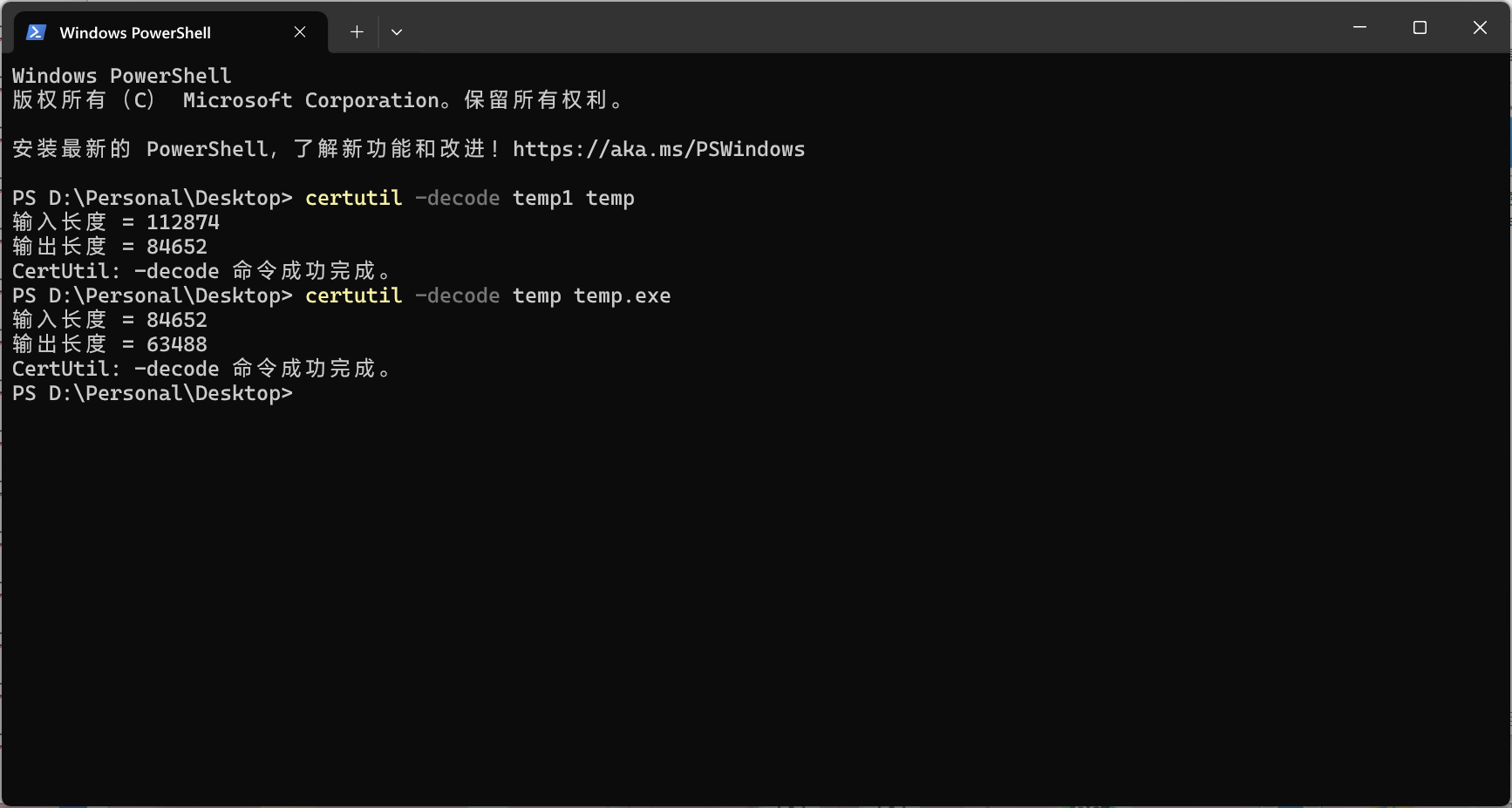
得到exe。
main函数里就是个简单的位移加密,别忘了之前还有异或7,直接写exp:
# 硬编码的数组
v7 = [
4288, 4480, 5376, 4352, 5312, 4160, 7936, 5184, 6464, 6528, 5632, 3456,
7424, 5632, 6336, 6528, 6720, 6144, 6272, 7488, 6656, 7296, 7424, 2432,
2432, 2432, 5632, 4416, 3456, 7168, 6528, 7488, 6272, 5632, 3520, 6208,
5632, 4736, 6528, 6400, 7488, 3520, 5632, 5184, 3456, 7488, 7296, 3200,
6272, 7424, 2432, 2432, 2432, 7808
]
# 解密字符的操作:将数组中的值右移6位
decrypted_chars = [chr(value >> 6) for value in v7]
# 从第七个字符开始,进行异或操作
for i in range(6, len(decrypted_chars)):
decrypted_chars[i] = chr(ord(decrypted_chars[i]) ^ 7)
# 将解密后的字符拼接成字符串
decrypted_string = ''.join(decrypted_chars)
# 输出解密后的字符串
print("Decrypted string:", decrypted_string)
#CFTDSA{Vba_1s_dangerous!!!_B1ware_0f_Macr0_V1ru5es!!!}(有点小问题,改一下就行)